13 AI Cybersecurity Tools For More Effective Protection in 2022
For both small-scale and large-scale organizations, it is vital to consider cybersecurity a top priority. Cybersecurity is a critical issue for businesses, and yet it remains one of the most difficult to address.
There are many different ways to secure your business, but one of the best ways is using AI tools. AI can help you identify any security threats before they happen, and it can also help you fix any issues that may have arisen.
In this light, we listed the best AI cybersecurity tools that can ensure that your company is always protected from malicious attacks.
- , Software

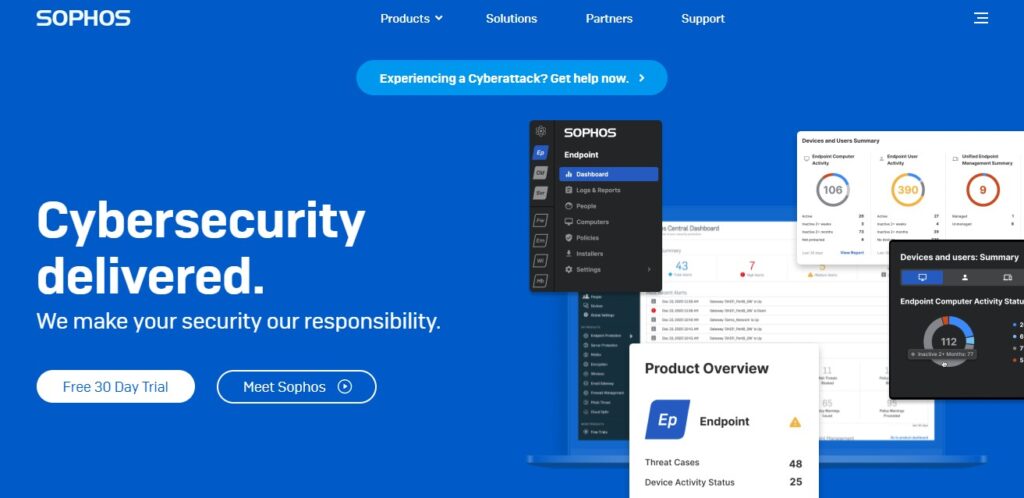
Sophos allows you to install a local agent on each PC or Mac that requires protection. And it controls all of the settings from a web-based dashboard. Given that the IT department maintains security remotely in a commercial context, this makes perfect sense. There is a limit of three installs per subscription.
The web dashboard is where all configuration and logging takes place. Given the product’s corporate beginnings, this makes a lot of sense. IT teams control antiviral from a centralized interface, rather than relying on inexperienced personnel to keep things operating. The dashboard shows all of the devices you have secured, each with a number signifying unread notifications.
For further information and setup choices, select any device, or click Add Device to add protection to another PC or Mac. You may either click to download and install it on your existing machine or copy a link to share with others. It installs Sophos and links the installation to your account for remote management in either case.
When you choose a device, a screen with five tabs appears: Status, History, Protection, Web Filtering, and Privacy. Antivirus Protection, Web Protection, Ransomware Protection, Privacy Protection, and Malicious Traffic Detection are the five protective components represented on the Status page.
On the History tab, you can view a record of everything Sophos has done to protect you, as well as filter by event type. Webcam Protection is the only feature on the Privacy tab, and Web Filtering allows you to customize the parental control system.
Even for an individual who does not run a business, this allows you to set up security for any friend or family member and handle any issues without having to pay them a visit or try to talk them through it over the phone.
💡 Recommended Reading
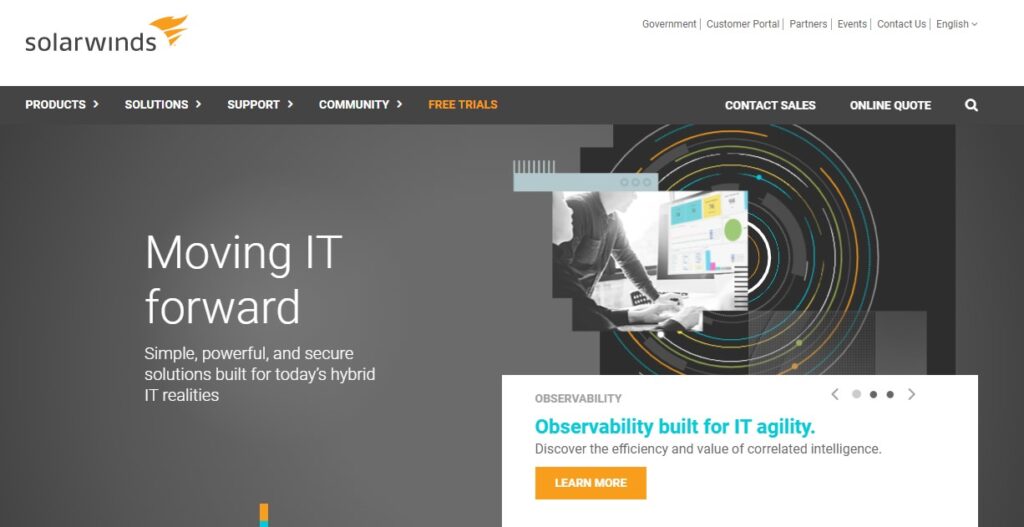
SolarWinds is a leader in IT management software development. One of its most important products is the SolarWinds Network Performance Monitor (NPM). This system is dedicated to keeping track of the health of networked devices. Network equipment, such as routers and switches, endpoint devices, such as terminals, desktop PCs, and mobile devices, as well as office equipment, such as printers, are among the hardware that SolarWinds NPM monitors. The continuous monitoring procedure collects data for troubleshooting purposes.
With economical, easy-to-use network monitoring software like Solarwi, you can reduce network disruptions and rapidly discover, diagnose, and repair network performance issues. You can get sophisticated network troubleshooting for on-premises, hybrid, and cloud services with SolarWinds Network Performance Monitor (NPM), which includes critical route hop-by-hop analysis.
The NPM offers a dashboard with extensive features that allow you to personalize your network data views and filter the events that the system reports. This is an extremely adaptable system that can handle any network size. The NPM package is self-contained.
The Network Performance Monitor’s working processes are based on the Simple Network Monitoring Protocol. This is a network industry standard that requires every device to have an agent application installed. As part of its firmware, every device that can connect to a network will already have an SNMP agent installed. The Network Performance Monitor offers the central controller that SNMP demands.
Although you might be tempted to use the Network Performance Monitor on a small network, its capabilities are best suited to medium to large networks. Its additional features and visualizations will significantly improve network management efficiency and network stability for big and complex networks.
GoTo Resolve is a remote support and service management solution that allows IT teams to remotely access and troubleshoot end-user devices, regardless of their location.
GoTo Resolve is designed to help IT teams improve their efficiency and reduce the time it takes to resolve technical issues. It aims to provide a comprehensive remote support solution that simplifies the process of managing and troubleshooting end-user devices.
GoTo’s IT Management platform features a security architecture designed to protect an organization’s network and data. This includes multi-factor authentication, encryption, and regular security updates to keep systems safe from potential threats.
The platform also offers monitoring and reporting capabilities to help IT teams stay informed and respond to potential security issues in a timely manner. Overall, the security architecture of the GoTo IT Management platform aims to provide a comprehensive and secure solution for organizations to manage and protect their IT systems.
Perimeter 81 is a prominent network cybersecurity solution for enterprises throughout the world, providing secure remote access and network capabilities through a multi-tenant cloud that is extremely scalable. Perimeter 81 is the preferred network security solution for thousands of organizations, ranging from small businesses to major corporations. Perimeter 81 interfaces easily with key cloud service providers, allowing you to safeguard cloud and on-premises resources.
With Perimeter 81’s all-in-one cloud administration platform, you can simply migrate your resources to the cloud, control team member access from anywhere, and receive network insight. You can secure and manage your network with just a few clicks with features like Firewall as a Service, Device Posture Check, Web Filtering, and more.
Your workers – and no one else – can access your company’s internal network thanks to the dedicated servers and IP addresses this has. In other words, no one will be able to access these resources unless they are connected to a dedicated VPN server, safeguarding your sensitive data from unauthorized access.
A VPN account’s security is enhanced with two-factor authentication. And, when it comes to enterprises, you should use as many levels of protection as possible. And surely, Perimeter 81 can help with it. When using Perimeter 81, there are several ways to deploy two-factor authentication. Your workers can prove their identity by receiving a distinctive security code via SMS or push notification, typing out the Google Authenticator unique number sequence, or utilizing the extra-convenient Duo Security app when checking in to their account.
Vipre protects against both classic viruses and new threats such as malware, Trojans, rootkits, and more. Its Advanced Active Protection offers real-time protection, which is a key element of any antivirus or antimalware program. And Vipre pulls it off admirably. The antivirus performs exceptionally well in AV-Comparatives’ independent virus detection testing. It identified 96.8% of threats during the most recent testing session, with only four false positives. To put it another way, Vipre has a very good probability of identifying a danger before it may affect your device.
A comprehensive scan, a rapid scan, or a bespoke scan are all options of this software. Also, while you can view the history of the scans completed, you cannot see how long each scan took. The scans themselves are quite adaptable. You can, for example, scan external disks, restrict specific apps from scans, and have Vipre do a second layer scan if the rapid scan detects a danger.
Vipre’s email protection function comes in handy for Outlook users. You can add email addresses that you want to be tagged as spam manually. Incoming email is also scanned for viruses, and risks are instantly quarantined. If you want the application to automatically detect questionable emails that could try to steal personal information from you, keep the anti-phishing toggle on.
The Secure File Eraser function allows you to remove all undesirable files from your PC. Simply right-click on the folder or file you wish to delete and select the relevant option from the menu.

To safeguard your organization from fraud, don’t forgo a seamless, frictionless onboarding process. SEON’s strong digital footprint analysis ensures you can quickly identify high-risk individuals, prevent account takeovers, and deliver a consistent customer experience while remaining compliant. You can create a comprehensive user profile to guarantee that chargeback rates, friendly fraud, and account takeovers are all minimized in real-time. SEON is on a quest to make fraud detection more accessible to all internet businesses. They use artificial intelligence and machine learning to make fraud protection accessible to all organizations and tough for criminals to defeat.
With two primary solutions, SEON’s products are developed around two basic goals: provide effective risk prevention and provide organizations choice in how they combat fraud. The SEON Intelligence Tool is a data enrichment service that gathers open, social data points about a customer’s digital footprint. To speed up manual reviews and the risk management process, it can be utilized as a one-click Chrome plugin or through API.
The main end-to-end solution is the SEON Sense Platform. It is used to analyze users’ online behavior using velocity rules, software and hardware setup using device fingerprinting, and enhance data in real-time using email, phone, and IP analysis, as well as social media profiling. Data is sent into an automated, machine-learning-based system that employs predictive risk assessment to automate decision-making and streamline manual evaluations. Accessible through API or a GUI with complete team administration capabilities.
REVE Antivirus is an IT Security program for home users and businesses that protects against viruses, spyware, and other malware. It includes anti-rootkit, anti-spam, data theft prevention, and parental control with live notification. Much more precisely, REVE Antivirus for Android is a security and privacy app. It has both internal and external media scanning capabilities, as well as extensive remote lock-down capabilities. The phone scanner, which scans both applications and external storage directories, the running app scanner, and a custom scan are the three scanning modes available in REVE.
The default phone scanner takes its time when it comes to examining your phone. REVE has the type of many thorough scanning features. REVE allows users to check for virus definition updates manually as well as establish an automated update check period of every twelve hours, every day, or every two days.
REVE’s web dashboard allows customers to remotely locate, lock, and erase their devices using the anti-theft security module. Alarms can also be set off remotely to deter burglars. Users may utilize the web-based interface to manage numerous REVE devices or designate a trusted number to send encoded text messages to activate the lock-down functionality. The app also features a privacy assessment tool that rates each app based on the number of permissions it requests and assigns an overall risk rating to your device. A list of the rights given to each app is displayed when you click on it.
The app’s parental control button is designed to provide the user administrative control over other REVE-connected devices.
The numerous features in Iolo System Mechanic allow you to clean up a sluggish PC, safely erase data, and execute other computer-related system activities. When a PC’s performance comes to a crawl, it is irritating, but it does not imply you need to buy a new machine. With a few clicks, a tune-up software like Iolo System Mechanic can get your system back in shape.
Iolo System Mechanic enhances the efficiency of your computer by defragging the hard drive, eliminating trash files, modifying CPU and RAM use in real-time, and doing other computer-enhancing operations. In addition, the current edition enhances some long-standing functions while also introducing a new, appealing interface.
The newest version of Iolo System Mechanic features a fresh, simplified style that makes finding the app’s numerous capabilities easier than ever. The left pane of the interface has specific tune-up subcategories, such as ActiveCare (real-time system monitoring and cleanup) and LiveBoost (maximizes CPU, RAM, and hard drive performance). Furthermore, helpful chat bubbles appear to explain typical PC issues as well as the tools’ many functionalities. Individual tools can be activated or a one-click tune-up can be started.
After you run Iolo System Mechanic, the Dashboard appears by default. If Iolo finds an issue, the Repair Now button shows here. When you click the icon, Iolo launches the proper system-cleaning tools to remove garbage files, unwanted applications, and other issues.
In Darktrace, machine learning and probabilistic mathematics have been used to create a self-configuring cyber protection system. For threat detection, response management, and incident tracking application for enterprises of all sizes, this is a great tool as an AI Cybersecurity tool.
Darktrace was the first business to design an AI system for cyber security, having been founded in 2013 by mathematicians from the University of Cambridge. It became evident soon that the system could detect a wide range of threats at an early stage, including insider assaults, latent vulnerabilities, cloud-based threats, and even state-sponsored espionage.
Darktrace’s AI leadership was cemented in 2016 with the release of Darktrace Antigena, the first-ever autonomous reaction technology. The Enterprise Immune System was able to react to in-progress cyber-attacks in a very accurate manner thanks to this invention, providing security professionals the time they badly needed to catch up. When the WannaCry ransomware assault impacted hundreds of businesses in 2017, Darktrace Antigena reacted in seconds, saving client networks from irreversible harm.
Darktrace is a global leader in autonomous cyber AI and provides a variety of useful tools to deliver a wide range of excellent assistance and superior threat security. Darktrace integrates with a variety of prominent platforms, including Microsoft 365, Azure, AWS, and others.
IBM Security QRadar assists security teams in detecting, understanding, and prioritizing threats that are most important to the company. The system collects data from assets, clouds, networks, endpoints, and users, correlates it with vulnerability and threat intelligence and uses advanced analytics to identify and monitor the most significant threats as they travel through the kill chain.
Once a serious threat has been found, AI-powered investigations give businesses immediate, intelligent insights into the attack’s underlying cause and scope, allowing them to up-level their first-line security analysts, speed security operations procedures, and decrease the incident impact. Managing an expanding number of cloud apps requires an open, linked strategy.
For a full XDR strategy, QRadar allows you to combine your EDR, SIEM, NDR, SOAR, and Threat Intelligence while leaving data in place. Using IBM and open third-party connections, you can connect your existing tools and automate your SOC.
Balbix uses specialized AI to assess the business attack surface and deliver a 100x more accurate perspective of breach risk. Vulnerabilities and other risk items are continually identified and prioritized by the platform, which then dispatches them for automated and supervised remediation.
Balbix helps you minimize cyber risk by 95% while doubling the efficiency of your security staff. The majority of data breaches occur as a result of known security flaws that are overlooked and not addressed. Security teams are attempting to identify and address vulnerabilities, but they are unable to keep up.
Balbix regularly analyzes up to several hundred billion time-varying data from your network to correctly evaluate breach risk.
Acunetix (from Invicti) is an automated application security testing platform that allows small security teams to take on large application security concerns. Acunetix helps enterprises decrease risk across all sorts of online applications with quick scanning, comprehensive findings, and intelligent automation.
Security teams can use Acunetix to work more fluidly with developers and save time and money by automating tedious security procedures This can ensure that every online application has been crawled completely. So, it makes it a possibility to make web application security a priority rather than an afterthought.
Site crawling, analysis, threat identification, SQL injection testing, network scanning, and testing are all important functions of this. Its vulnerability scanner uses the black box and grey box approaches to crawl through open-source software and custom-built applications. Users may test routers, firewalls, and switches, as well as discover misconfigurations, using the network security module.
Syxsense keeps desktops, laptops, servers, and remote users up to speed with the latest security patches and software upgrades from Microsoft, Windows 10 Feature Updates, macOS, Linux, and third-party suppliers including Adobe, Java, and Chrome. Patch virtual machines, legacy operating systems, and IoT devices as well! Patch commands like Critical, Top 10 Windows, and so on.
This is best for IT professionals and organizations. Syxsense integrates all of the tools required to keep endpoint devices up to date (patch management), allow remote management of endpoint devices (device management), and detect and remediate security vulnerabilities from a single console, whereas most endpoint solutions require multiple tools, agents, and consoles to address these combined threats.
It is built on the Syxsense Cortex workflow automation platform. An easy-to-use editor for developing remediation processes avoids the need for extensive remedial scripts with this application.
AI Cybersecurity Tools Final Words
This article discussed the best AI Cybersecurity Tools that businesses and organizations can make use of. Now, you are good to go and make maximum use of these.
Patryk Miszczak


